Quick Summary: In our comprehensive guide, we delve into the intricacies of managing connection strings and API keys in Power Automate. Learn crucial strategies to safeguard sensitive information, streamline workflows, and ensure the security of your automated processes. Stay ahead in the world of efficient automation.
Introduction:
Power Automate, Microsoft's cloud-based service for automating workflows and business processes, empowers users to create seamless integrations between various applications and services. When working with Power Automate, managing sensitive information such as connection strings and API keys is crucial for maintaining security and ensuring the smooth functioning of your automated processes. In this article, we will explore best practices for handling connection strings and API keys in code within Power Automate.
Open Power Query Editor:
In Power BI Desktop, click on "Edit Queries" on the "Home" tab to open the Power Query Editor.
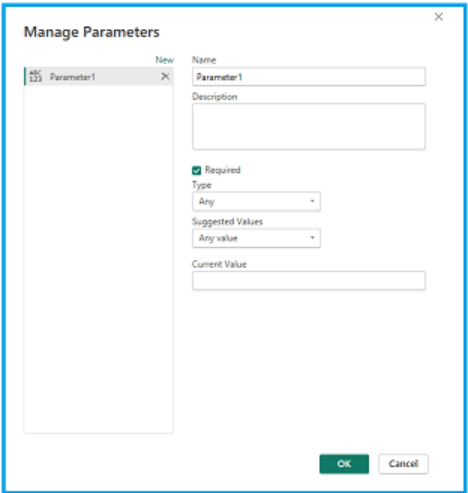
Create a New Parameter:
In the Power Query Editor, go to the "Home" tab.
Click on "Manage Parameters."
Define a New Parameter:
In the "Manage Parameters" dialog, click on "New Parameter."
Configure Parameter Settings
In the "Create Parameter" dialog, provide the following information:
- Name: Give your parameter a descriptive name (e.g., "ConnectionString").
- Description (optional): Add a brief description to help users understand the parameter's purpose.
- Type: Choose the appropriate data type for your parameter (e.g., Text for a connection string).
- Current Value: Set the initial value for your parameter. This can be a placeholder or a default value.
Usage in Queries:
Once your parameter is created, you can reference it in your Power Query queries.
For example, if you have a connection string in your query, replace the connection string with the parameter name.
To do this, select the part of the query where the connection string is used, and then replace it with `ParameterName`.
Apply Changes:
After making changes to your queries, click "Close & Apply" in the Power Query Editor to apply the changes to your Power BI report.
Configure Parameter Refresh Options
When you publish your report to the Power BI Service, you can configure how parameters should be managed during refresh.
You can choose to prompt users for parameter values, use default values, or specify parameter values for different environments.
Testing and Deployment:
Test your report to ensure that the parameterization of the connection string works as expected.
When deploying to different environments (e.g., development, production), configure the parameter values accordingly.
Ready to supercharge your business processes with Power Automate?
Hire our skilled Power Automate developers to automate workflows and boost efficiency.
Implement Role-Based Access Control (RBAC):
To control access to sensitive information, leverage Power Automate's role-based access control. Define roles and permissions based on user responsibilities, ensuring that only authorized individuals can view or modify connection strings and API keys. RBAC adds an extra layer of security, mitigating the risk of unauthorized access or tampering.
Regularly Rotate Credentials:
Security best practices recommend regularly rotating credentials to reduce the risk of unauthorized access. Power Automate allows you to automate credential rotation using scheduled workflows. Implement a routine to update connection strings and API keys at predefined intervals, keeping your automated processes secure and up-to-date.
Logging and Monitoring:
Implement robust logging and monitoring mechanisms to track the usage of connection strings and API keys within your workflows. Set up alerts to notify administrators of any suspicious activities, ensuring prompt response to potential security incidents. Monitoring provides visibility into credential usage, helping you identify and address security concerns proactively.
Encrypt Sensitive Data:
When dealing with sensitive information, encrypting data in transit and at rest is essential. Ensure that your Power Automate workflows adhere to encryption best practices. Use HTTPS for secure communication and leverage encryption options provided by external services when storing sensitive data.
Educate Users on Security Practices:
Security is a shared responsibility. Educate users and administrators on security best practices when working with connection strings and API keys in Power Automate. Encourage the use of strong, unique passwords and promote awareness of potential security threats, such as phishing attacks.
Regularly Review and Update Security Policies:
As the threat landscape evolves, it's crucial to review and update security policies regularly. Stay informed about new security features and enhancements in Power Automate, and adjust your security practices accordingly. Regular reviews ensure that your automated processes remain resilient against emerging security threats.
Conditional Access Policies:
Take advantage of Azure's Conditional Access Policies to enforce additional security measures. Conditional Access allows you to set conditions that must be met before granting access, such as multi-factor authentication or device compliance checks. Integrating Power Automate with Conditional Access policies adds an extra layer of security, especially for workflows that involve critical business processes.
Secrets Management Best Practices:
When working with Azure Key Vault or other secrets management solutions, adhere to best practices. Implement proper access controls within the secrets management system, regularly rotate secrets, and monitor for any unauthorized access. Additionally, consider using Managed Identities in Azure to simplify authentication and eliminate the need for explicit API keys in your Power Automate workflows.
Role-Based Access for Power Platform:
Extend role-based access controls beyond Power Automate to cover the entire Power Platform ecosystem. By defining roles and permissions across Power BI, Power Apps, and Power Automate, you ensure a holistic approach to security within the Microsoft Power Platform. This centralized management simplifies user access controls and reduces the risk of unauthorized access to sensitive information.
Conclusion
By following these steps, you can create and use parameters in Power Query to manage configuration values like connection strings or API keys centrally. This approach makes it easier to maintain and update these values across multiple reports or dataflows and allows for better separation of configuration from your report logic.
Effectively managing connection strings and API keys in Power Automate is essential for building secure and reliable automated workflows. By following these best practices, you can enhance the security of your Power Automate solutions, reduce the risk of unauthorized access, and ensure the smooth operation of your business processes. Stay vigilant, stay secure!
Hire our skilled Power Automate developers to automate workflows, boost efficiency, and unlock the full potential of your organization. Let's transform your operations together!








